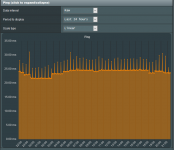
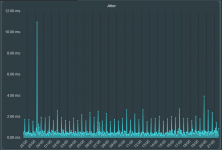
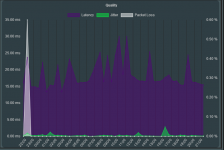
No, I`m referring to the block-outside-dns parameter that they are pushing. Filtering it out will suppress the log warning.
Thanks for the info. Whenever I enable the VPN this info appears in my log file. What is it and is it something to worry about?
Jul 5 18:14:27 ovpn-client1[3930]: WARNING: --ping should normally be used with --ping-restart or --ping-exit
Jul 5 18:14:27 ovpn-client1[3930]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Jul 5 18:14:27 ovpn-client1[3930]: WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1633', remote='link-mtu 1581'
Jul 5 18:14:27 ovpn-client1[3930]: WARNING: 'auth' is used inconsistently, local='auth SHA512', remote='auth [null-digest]'
Jul 5 18:14:28 ovpn-client1[3930]: WARNING: You have specified redirect-gateway and redirect-private at the same time (or the same option multiple times). This is not well supported and may lead to unexpected results
Jul 5 18:14:30 ovpn-client1[3930]: WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Then when I exit the VPN I get this in log file. Anything to worry about?
Jul 5 18:17:46 ovpn-client1[3930]: event_wait : Interrupted system call (code=4)
Thanks again for the info and help....